- Azure active directory :- Direct tab is there or you can go via services
- When a subscription is created it gets its own tenant. Its a place where the users of your organisation only are managed.
- The Azure AD tenant is the container for users and groups that you want to give access to resources in azure. example like deploying web apps or create containers in azure blob storage or it could be user identities for end users for accessing a web application or uploading data to the file storage.
- USERS:- The panel which opens with details is called blade. This is the place where the users in this directory are listed. you can manually add the users here. There is a column called on premises sync enabled(you can actually synchronize your on-premise active directory with this azure active directory tenant and then assign those on premises users permission in azure). you can do that by downloading and installing a tool on premises called Azure AD sync
- Two options to create user. Either create new user – whether you want to create user identitiy here in this azure ad tenant or you want to invite an external user
- External users are part of something called azure B2B collaboration or business to business. Thats for users outside your org who are not part of azure active directory tenant and lets it give them access to applications or services. They become an object in your azure active directory that you can assign permission to. But their sign in process is handled by their own extenrnal identity provider.
- Once the user is created. You can the user to the groups. Groups lets you create , groups of users so that you can assign roles to either individual users or to the groups. Those roles are used to provide access to the resources in the subscription. Using group is not mandatory . only user creation is sufficient enough. But group helps you manage it better. It makes your life easy. Assign that user global admistrator role that will allow them to perform any action in azure.
- Licenses:- By default azure ad tenant has the azure active directory free license , but there are other licenses that are available that you can assign to individual users like azure premium p1 or p2 licenses. These give users additional features like being eligible conditional access policies
- Conditional access policies
- They allow azure to make authorization decisions based on things like azure AD groups that the user belongs to or the location the user is coming from and characteristics about the device they are using
- Conditional access policies can also work with azure AD identity protection which uses machine learning to identify the risky sign-in behavior
- If the user is approved to sign in after the conditional access policies , you can also choose to enforce multifactor authentication . This is done by a service called azure multi factor authentication
- you can use azure MFA with conditional access policies if your users have at least an azure AD premium P1 license. You can also enable it for individual users so that they always has to use multi-factor authentication
- Another thing in Azure AD is app registrations which represent an application like mobile app or web app or web api
- It creates trust relationship between your app and Azure AD
- Then those applications can use Azure AD to log in their users
- Azure AD Connect:- you can sync your on premise active directory with the azure ad tenant. you can download the tool to install it on-premises from this blade, then you have options on how to set up that connection either directly or federation with a tool like AD FS.
- You can add your own domain name to this azure ad tenant.
- you can verify that custom domain name in azure
- Now that domain name can be used while creating users.
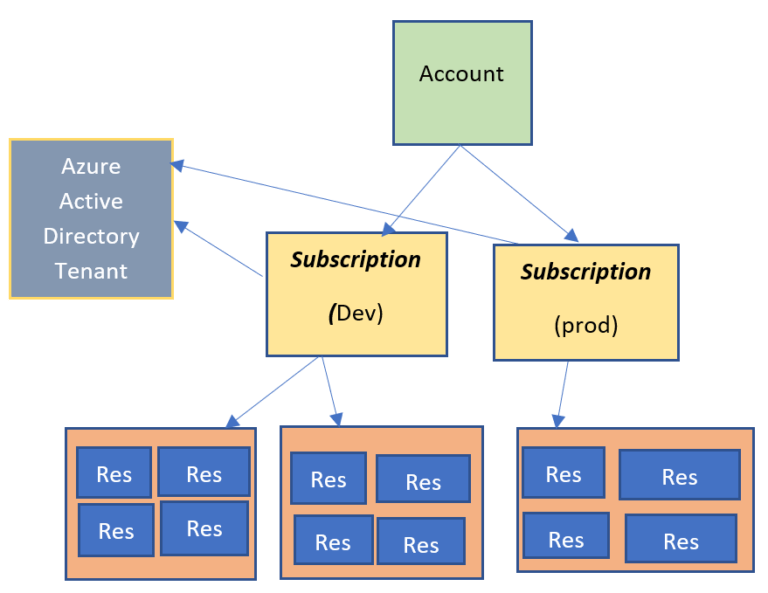
- An azure account is referred to as billing account in the documentation. Its an entity that have subscription. I can create multiple subscriptions and access all of them when I log in.
- Free account we created
- Also it has pay-as-you-go accounts that charge the credit card for the resources consumed
- Visuals studio subscriber accounts that are basically pay-as-you-go accounts with some free credits.
- There are also enterprise agreements for organizations.
- You can continue with the free trial subscription + and also create pay-as-you-go subscription or I could upgrade the free trial subscription to pay as you go
- Each of the subscription gets an invoice showing the resources that were consumed each month . And each subscription has a payment method , a credit card.
- Within subscription resources are created and they are actually created within resource groups
- When we signed up for the azure free trial account , subscription was created and there was azure active directory tenant created too . so you might assume there is one to one relationship from subscription to azure active directory tenant but it doesnt has to be .
- Multiple subscription can have trust relationship with the same azure active directory tenant
- Each subscription can be linked only to one azure active directory tenant
- An account can have multiple subscriptions. Subscription contain multiple resource groups. Resouce group contain resources . A resource can only belong to single resource group. And subscription has trust relationship with azure active directory tenant. The subscription trusts azure active directory tenant to authenticate users , services and devices.
- You can have multiple subscriptions trust the same azure ad tenant , but each subscription can only trust single directory, and all of users have a single home directory for authentication , but each user can be a guest in other directories
- Why multiple subscription ??
- you might want individual subscriptions for different environments like dev, prod and be able to apply separate access to manage each subscription using role based access control . Or you might want to keep resource separate in different subscriptions to make billing easier coz each subs can provide a bill for the resource that it uses.
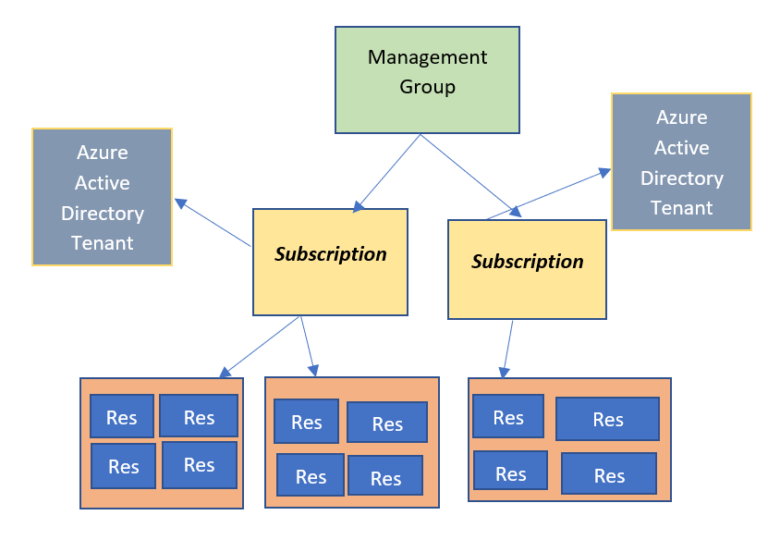
- Having multiple subscription could be nightmare. But we have something called management groups that makes it easier
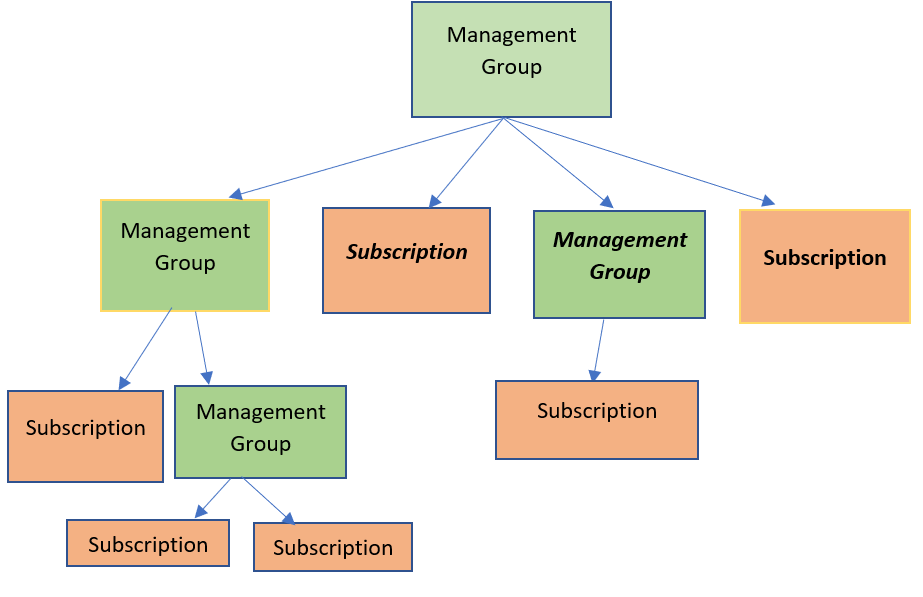
- management group contains multiple subscriptions. They can contain other management groups so you can create the hierarchy
- you can manage security on management group level
- permission given at the management group level will get inherited by management groups and subscriptions underneath
- All the subscriptions under the management group need to trust the same azure active directory tenant
- There is something in azure called policies – these allows you to set the rules like virtual machines can only get created in the East US region. Then you apply that policy to subscription or at the management group level and it gets enforced and reported on.
- built in policy – using tags – simple policy
- complex policy
- FedRamp High
- Hippa policy
- you can create your own custom policies and apply to your management group and subscriptions.
Extra points
- AZURE APP SERVICES – to host application
- Storage account – for storing files
- Server less options
- azure functions
- azure logic apps
- portal
- portal.azure.com – adm tool for azure
- once you create the account, you get adm account id
- you can create individual users and assign them permissions. So no need to keep using the administrative account to login , and you should not as it has superuser privileges