JWT Basics
- standardized security token format that
allows you to create json payload that you can send to another party without the fear of any
tampering [TAMPER PROOF] - Json web token has three parts. Each
sections is separated by a dot. - Look the initial 3 letters. It is always eyJ –> base 64 encoded ,when decoded –> eyJ = base64({“)
- securely transmit data between systems
- Once Jot is issued, its immutable and cannot be
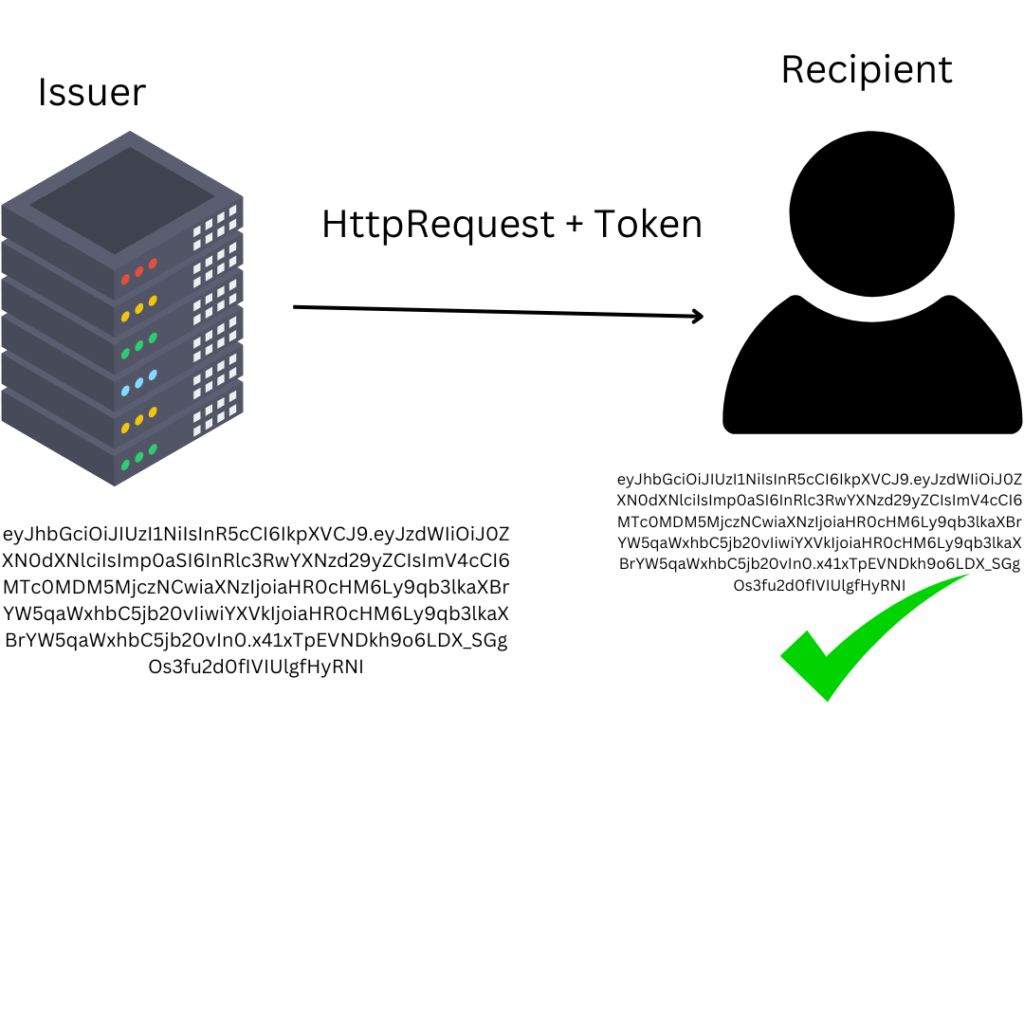
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiJ0ZXN0dXNlciIsImp0aSI6InRlc3RwYXNzd29yZCIsImV4cCI6MTc0MDM5MjczNCwiaXNzIjoiaHR0cHM6Ly9qb3lkaXBrYW5qaWxhbC5jb20vIiwiYXVkIjoiaHR0cHM6Ly9qb3lkaXBrYW5qaWxhbC5jb20vIn0.x41xTpEVNDkh9o6LDX_SGgOs3fu2d0fIVIUlgfHyRNI
Anatomy of JWT
- Header
- Payload
- Signature
They are always encoded but not encrypted. So you are not supposed to store the secretive information inside jwt.
Claims – are unique identifier (jti – jot token identifier) + users email or roles
